
Writeup: Crate CTF - Intern 2 (OSINT)
Writeup Crate CTF - Intern 2 (OSINT)
Crate CTF - Intern 2 (OSINT)
A CTF Challenge from the crate CTF hosted by FOI. I think this was the most fun of the ones i managed to solve.
If you want to give this challenge, or another one a try they are still up. ctf.crate.foi.se
Objective
The objective of this challenge is to find a flag. The description is as follows (Translated to English):
Ossian Wallengren started an internship at Cyber Caching Inc. last year. Your task is to prepare for an upcoming pentest by gathering information about their infrastructure. According to information obtained, Ossian Wallengren stores login credentials for his workplace on his personal web server. Start by accessing his server. Note that content published on the internet before last year’s CTF competition (2023-11-18) is not relevant to this task.
Important! Due to the nature of this task, it is difficult to specify which addresses are acceptable to target, but it is possible to find the correct server in a way that does not appear more suspicious than a regular login. Do not send traffic that could be perceived as malicious (exploits, port scans, brute force attacks, etc.) to any server not explicitly designated as a target on this platform. This task can be solved using passive techniques without contacting any person.
The osint part
Since this is a osint challenge. The first thing is obviously to google “Osian Wallengren” and the company name.
I found:
- A linkedin profile
This was not very useful, he only seems to have shared some other peoples posts.
- A github profile
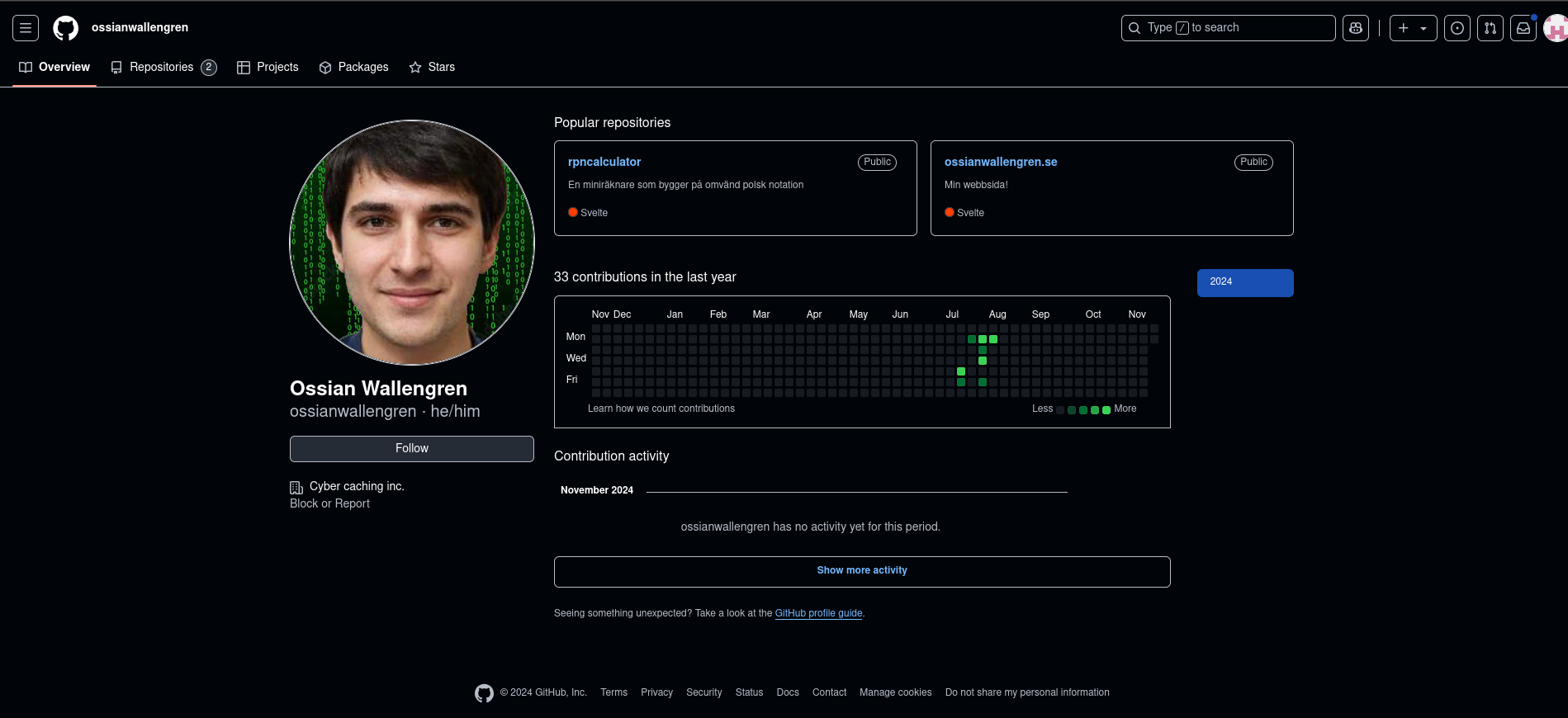
This is where it got interesting. As you can see, there is a Svelte repo, which has his link as the title.
First i did an nslookup on the domain. And found an ip.
❯ nslookup ossianwallengren.se
Non-authoritative answer:
Name: ossianwallengren.se
Address: 178.62.243.157
After this, i did an nmap scan on the ip.
❯ nmap -sC -sV 178.62.243.157
Starting Nmap 7.80 ( https://nmap.org ) at 2024-11-18 18:02 CET
Nmap scan report for 178.62.243.157
Host is up (0.019s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.7 (protocol 2.0)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
443/tcp closed https
And execpt for the website, there was an ssh server. Interesting!
So, i did visit the website. And found a blog post, about how to undo a commit when accidentally pushing secrets to a public repo.
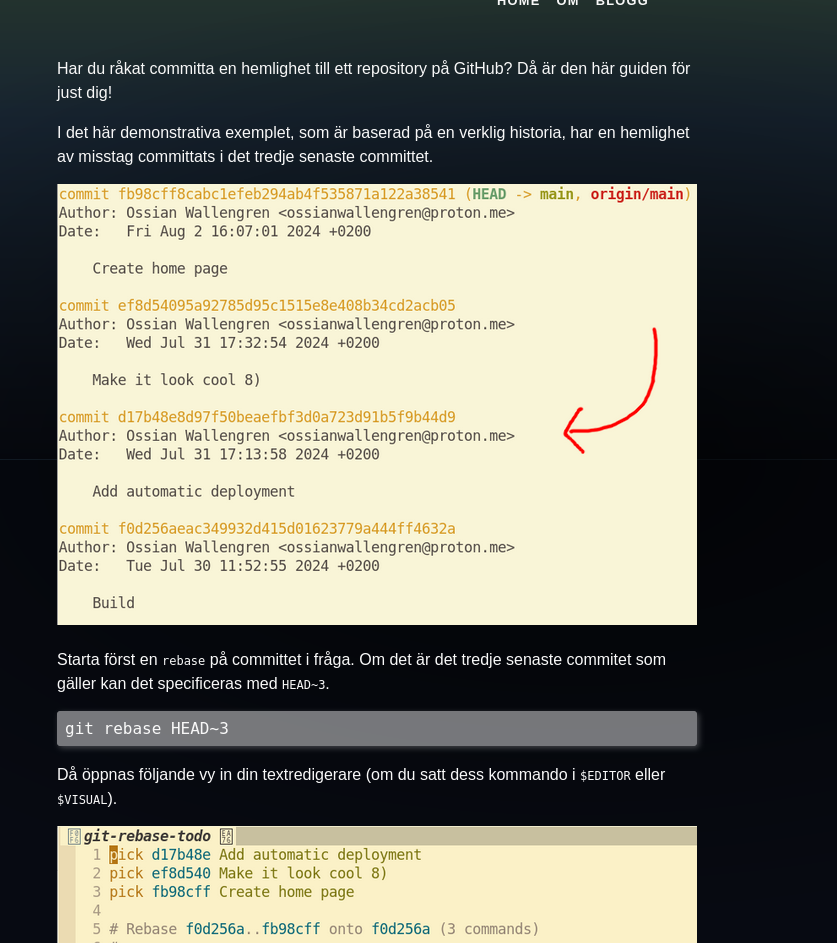
The first sentences translated to english:
Have you accidentally committed a secret to a repository on GitHub? Then this guide is just for you! In this demonstrative example, which is based on a true story, a secret was mistakenly committed in the third most recent commit.
This is interesting, because you can still access “deleted” commits if you have the commit hash. And the commit hash is shown in the blog post.
As in the picture, there is a arrow to the specific commit he screwed up in. As the commit still exist, you can still see it on github. And you only need the first 5 or so characters of the commit hash.
So by entering the first 5 characters of the commit hash, we can find the commit.
https://github.com/ossianwallengren/ossianwallengren.se/commit/d17b48
Now we can see the commit.
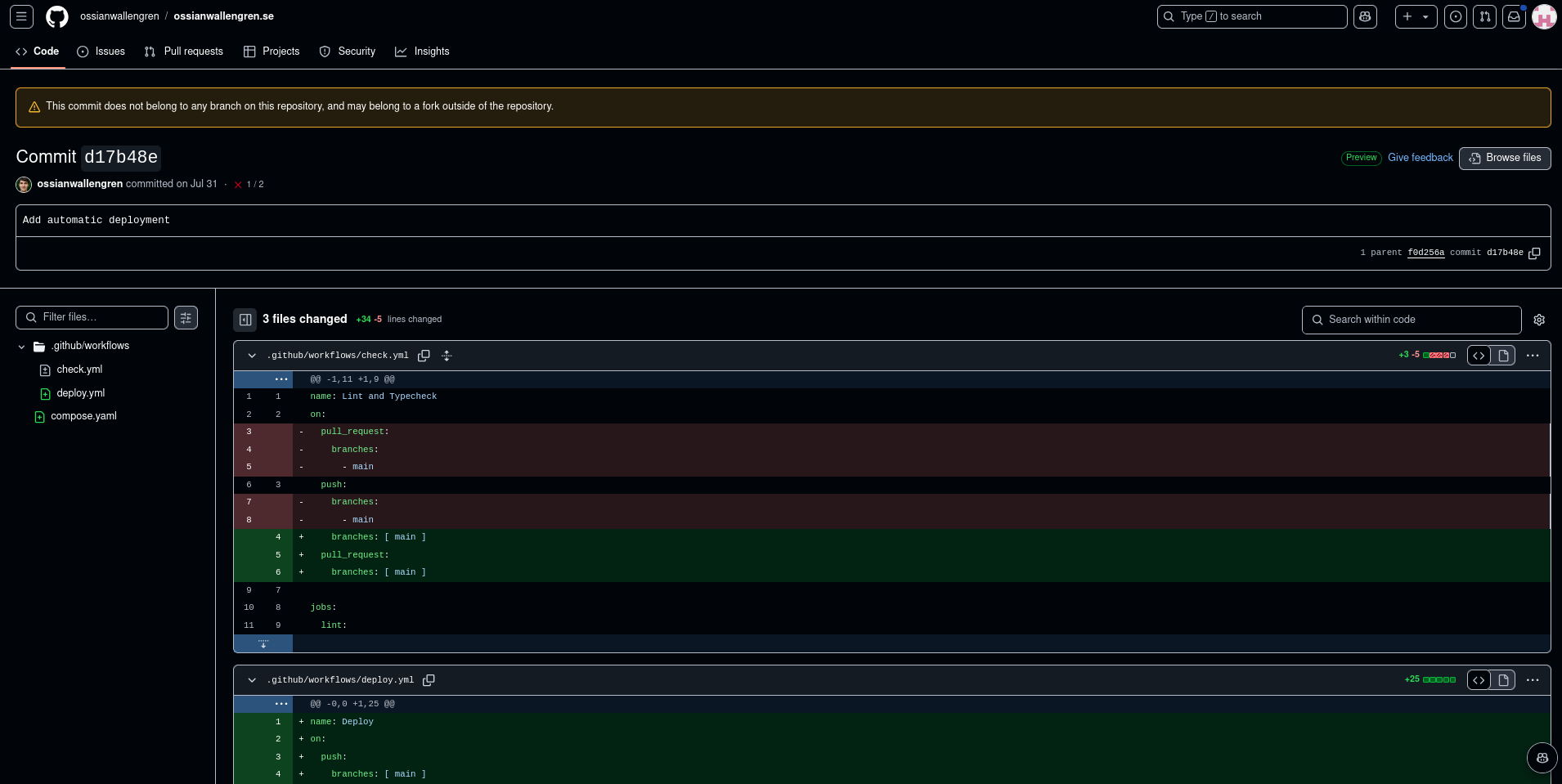
And we can see it is related to the github workflow-pipeline.
More specifically, this caught my eye:
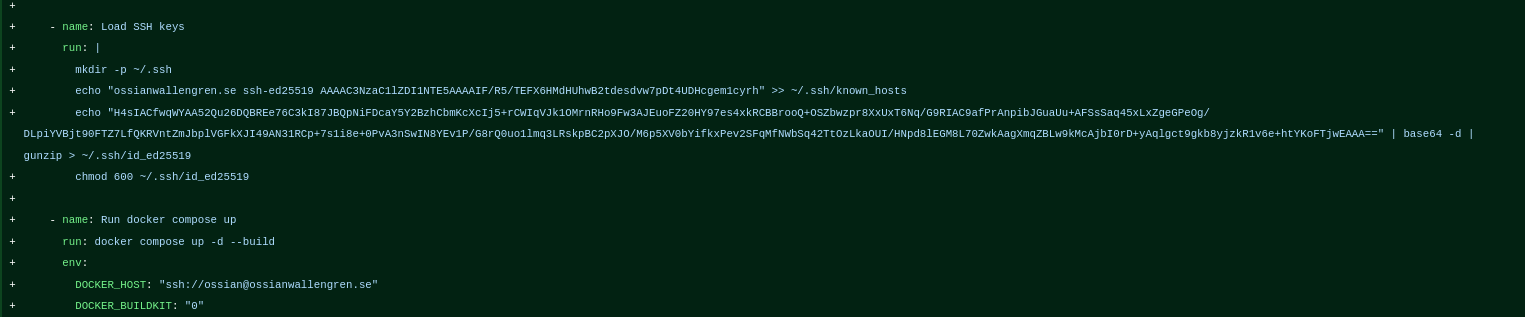
As we can see, there is a deploy pipeline, that creates a ~/.ssh/ dir, and add the host key to known_hosts, and lastly it decodes the base64-encoded ssh key and adds it as a key in ~/.ssh/
So, the whoopsie he did with that commit was the ssh-key not being injected as a environment variable.
Lets connect!
Lets do the same as the deploy pipeline. But i changed the name of the key.
❯ echo "H4sIACfwqWYA....." | base64 -d | gunzip > ~/.ssh/ossian
cat ~/.ssh/ossian
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACBTJGsDC6KrHBPj9P+4zqGMKkUVMiE1trAAopeqk/zrKgAAAJDrTS4o600u
KAAAAAtzc2gtZWQyNTUxOQAAACBTJGsDC6KrHBPj9P+4zqGMKkUVMiE1trAAopeqk/zrKg
AAAECpX2lQnjmE0ZBBnj9fYSoPl63VpmqScqeNL8bg1GXmf1MkawMLoqscE+P0/7jOoYwq
RRUyITW2sACil6qT/OsqAAAABm9zc2lhbgECAwQFBgc=
-----END OPENSSH PRIVATE KEY-----
We now got the private key!
Lets try it and see if we can login to the server.
❯ chmod 600 ~/.ssh/ossian
❯ ssh -i ~/.ssh/ossian ossian@ossianwallengren.se
ossianwallengren:~$ whoami
ossian
ossianwallengren:~$
And we are in!
The flag
ossianwallengren:~$ ls
flag.txt
ossianwallengren:~$ cat flag.txt
cratectf{den_där_guiden_funkade_ju_inte_alls}
ossianwallengren:~$
The flag is: cratectf{den_där_guiden_funkade_ju_inte_alls}
Which translates to: cratectf{this_guide_didnt_work_at_all}, refering to the blogpost.
Conclusion
This was a really fun challenge. This was the first year that OSINT was part of the CTF. And i hope we get some more OSINT challenges next year.